Don’t hire IP problems when recruiting
It’s often said that hiring decisions are the most important decisions made by managers and business owners. Would you be interested in bringing the following people on board?
The ‘sales gun’
You have an opportunity to hire the top sales person of your main competitor, Acme Co. She has an Outlook .pst file listing hundreds of potential clients and has great relationships with most of them. She has knowledge of the prices they pay, details of when their contracts expire, and ideas of how you could entice those customers away.
The software engineer
You’re considering hiring a senior software developer who has spent the last two years designing, developing and maintaining a software program for Acme Co. Acme Co has developed a competitive advantage through the way in which it captures customer information in its database and cross-references that information with its own data to match company products with customer needs. The software engineer knows he can’t re-use the code in your business but believes he can replicate the structure of ACME Co’s database for you, thereby closing the competitive gap.
Each of the above candidates brings risk to your business which requires management if you’re to avoid infringing Acme Co’s intellectual property (or ‘IP’). Both candidates could expose your business to the risk of misusing confidential information and infringing copyright, including, in the case of the software engineer, copyright that protects the structure of a database.
When people think about employees stealing IP from employers, the focus is usually on how innocent employers can protect their rights. However, when a new employee misappropriates the IP of a previous employer, this raises risks for three different parties:
- the previous employer, whose IP has been misused
- the employee, who can be personally liable for the misuse
- the new employer, who can be liable to the previous employer even if unaware of the misuse.

There are many reasons for the misuse of a previous employer’s IP
Opportunities abound
It’s easier than ever before for employees to take IP from their employers.
In the not-too-distant past, it was easy for businesses to quarantine sensitive and important IP. Confidential information might have existed in the form of hand‑written, hand‑drawn or typed documents such as drawings and diagrams, formulae, recipes, customer lists and contracts which could all be kept ‘under lock and key’.
Today, employees create sensitive intellectual property while working remotely. They have easy access to IP without being under the direct supervision of their employers. Even when working at the employer’s premises, it’s easy for employees to move IP to personal computers, smartphones and tablets, and not uncommon for them to upload IP to cloud-based file-sharing services.
Employees often don’t see it as a problem
Not only has it become easy to obtain IP from employers, but many employees also don’t see a problem with this.
In a global survey by Symantec, 62% of employees said it’s acceptable to transfer work documents to personal computers, and the majority of these never delete the data because they don’t see any harm in keeping it.
Interestingly, the same survey identified that many employees mistakenly attribute ownership of IP to the employees who created it rather than the employer who paid for it. For example, 59% of survey respondents from the US thought that a software developer had the right to re-use the code created for a former employer when this is not actually allowed. There is evidence that the same widespread misconceptions exist in Australia.
Some employers hope to benefit from hiring employees
The fault is not all with employees. Let’s face it, poaching a key employee from a competitor could give a business a significant boost while weakening the competitor at the same time. Many employers would be tempted to hire the candidates listed at the start of this article precisely for the ‘inside knowledge’ they can bring.
IP is becoming increasingly valuable
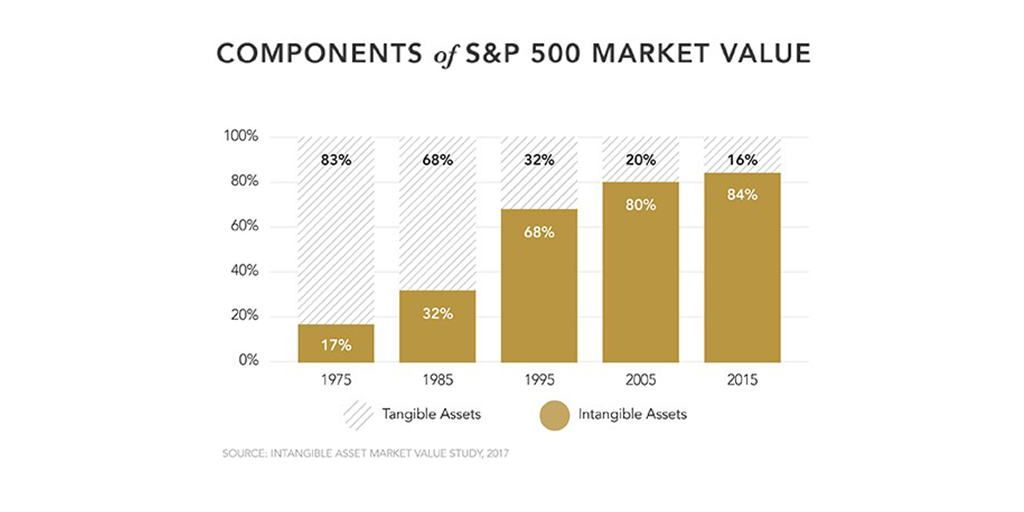
Intangible assets have become increasingly important as we evolve from manufacturing-based to information-based economies. According to the merchant bank Ocean Tomo, intangible assets (including IP) once represented a minority, but now constitute the vast majority, of the market value of the S&P 500:
How to minimise your risk
Understand the issues and assess your risks
As a business owner, you need to understand the risks and how they can materialise. You need to understand what sort of things can be protected by IP, how that IP can be infringed, and how to prevent or avoid those things from happening.
Be clear about your values and objectives
Once you’ve resolved not to infringe third party IP – perhaps for liability reasons, a corporate citizenship perspective, or both – you need to be clear about this in all of your dealings. You should set the tone internally, for example, by ensuring that you don’t target new recruits with the aim of gaining access to third-party IP. Your job ads should avoid any suggestion that you’re trolling for your competitors’ IP. Your personnel should be directed not to fish for confidential information during the interview process. Similarly, you should make it clear to candidates that you’re considering employing them for their professional skills and experience, and not for any specific knowledge, documents or information relating to, or owned by, their previous employers.
Protect yourself with contracts and policies
Contracts of employment should stipulate that employees must respect the IP of third parties, including past employers. Your contracts and policies might include a specific ban on using documents and electronic files produced for, or obtained from, previous employers.
Cover IP during your induction processes
Your induction process should promote and reinforce your culture of respect for third party IP rights. It should emphasise that if new employees try to utilise IP owned by their previous employers, they’re taking on personal legal risk from their old employers, bringing unwanted risk to your business, and breaching their employment contract with you. Induction training might also help employees to understand the difference between their skills and experience (which they’re allowed to bring to their new position) and confidential information (which they’re not). You might also help new employees to identify the general categories of information which would compromise your business if it were used or disclosed in their new job. This might include having patent and registered design searches performed on their previous employers and letting your new employees know that some of what they did for their previous employers may now be prevented by registrations identified in your searches.
Be savvy about input from new employees
It’s not enough to educate new employees and to hope that they’ll do as they’re asked. What happens if a new employee brings IP into your business from their previous employer despite being told not to? In many cases (infringements of copyright, patents and registered designs in particular), you can be found liable for intellectual property infringements even if you did the relevant acts innocently, and without any knowledge at all. While breach of confidence in sensitive information normally requires knowledge of some sort, you can be found liable if you had ‘constructive’ rather than ‘actual’ knowledge – i.e. you should have known that information was confidential even if you didn’t. You and your employees should have enough information to prevent or limit IP breaches by new employees. This may mean knowing what conversations to avoid, how to identify suspicious or risky behaviour, and what to do if the risks materialise.
Use a context-sensitive approach
The above suggestions need to be tailored to particular circumstances. It’s important to put risks into perspective for individual hires because some of the above measures will be minimum requirements in certain cases, but overkill in others. For example, the risks will generally be greater when incoming employees held senior positions at your competitors or held sensitive positions, with sales and product development being two areas requiring particular care. The risk will also be greater if you hire more than one employee from the same company: hiring your competitor’s entire New Product Development team is much riskier than just hiring a single graduate employee. Generally speaking, if the potential benefit from using IP belonging to your competitor is high, then you’re more likely to be sued, and your potential reputational and financial exposure is higher. Therefore, the measures you adopt need to be more stringent in these cases.
Plan for failure
Despite your best plans, things can go wrong. In these cases, be prepared to take the following steps:
Investigate
You need to understand what has happened. This includes being able to answer the following questions:
- what IP has been used?
- does it have much real or potential value, or could it be described as ‘trivial’?
- who has been involved?
- to what extent has it been used?
- how did the breakdown occur?
Implement appropriate measures
You need to take measures to prevent further breaches, to quarantine any unauthorised information, and to decontaminate your business (being careful not to do anything which could amount to destruction of evidence). You may also identify and implement preventative measures.
Seek legal advice
IP infringements can be extremely serious, and IP owners may seek urgent ‘interlocutory’ orders from a court. It’s best to obtain legal advice if you believe that you may have infringed the IP of a third party.